The only way to have an easy encrypted Time Machine backup is to use a directly attached storage device (Firewire, USB, Thunderbolt). That works fine for a desktop computer that stays in one place and you can just leave it plugged in all the time. But if I have to plug an external drive in to my laptop before starting Time Machine, it's not going to get done.
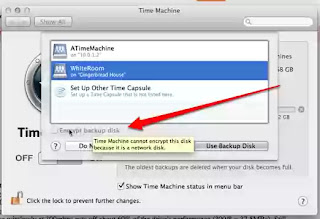
Time Machine volumes are supported on my NAS, but I don't want unencrypted backups so that anyone who steals the backup hardware has total access to all my files. That would be an especially ridiculous result for any who has bothered to enable Filevault (full disk encryption) on a machine. To make it clear, Time Machine backups are not encrypted, even when Filevault is enabled, unless you check that little box to make them so, which you can't if they are on a Time Capsule, NAS or any network volume.
The workaround is to create an encrypted disk image with a special filename, mount that, saving the password in your keychain, and use the "tmutil" terminal command to make Lion accept your Time Machine disk. Even this solution is still wanting, because you have to first mount the sparse bundle before Time Machine will do any work, and if the backup plan relies on me to do anything, it's not going to be reliable or regular.
Until I figure out whether something like iSCSI will work, I'll just keep doing intermittent Crashplan offsite backups (things copy only when I connect to a VPN) and the bi-monthly SuperDuper! disk clone, which is really inconvenient on a Macbook Air whose USB ports don't have enough bus power for a 500G external drive, forcing me to also haul out and get tethered to an AC adapter for the duration.



No comments:
Post a Comment